SPOT Managed Security

The Case for Managed Security Services
That is where we come in. While some try to sell tools as a solution, Fulcrum Group advocates that real cybersecurity needs processes around the tools, and people who understand the the right tools. Do you know where to start? Unless you have unlimited resources for cybersecurity, strategy before spending helps you maximize impact from your security investments.
HR Professionals expect an already challenging hiring environment to worsen
Majority expect the time it takes to fill open positions to increase
Majority expect the time it takes to fill open positions to increase
Basic Risk Management in Organizations
NIST Cybersecurity Framework
Identify
- Asset Management
- Business Environment
- Governance
- Risk Assessment
- Risk Management Strategy
Protect
- Access Control
- Awareness and Training
- Data Security
- Info Protection Processes and Procedures
- Maintenance
- Protective Technology
Detect
- Anomalies and Events
- Security Continuous Monitoring
- Detection Processes
Respond
- Response Planning
- Communications
- Analysis
- Mitigation
- Improvements
Recover
- Recovery Planning
- Improvements
- Communications
Don’t Have a False Sense of Cybersecurity
What to do to avoid becoming a target
- Use two-factor authentication
- Do not reuse or share passwords
- Use a password keeper/generator app
- Be sure to change the default credentials of the point-of-sale (PoS) controller or other hardware/software
- Ensure that you install software updates promptly so that vulnerabilities can be patched
SPOT Managed Security Services
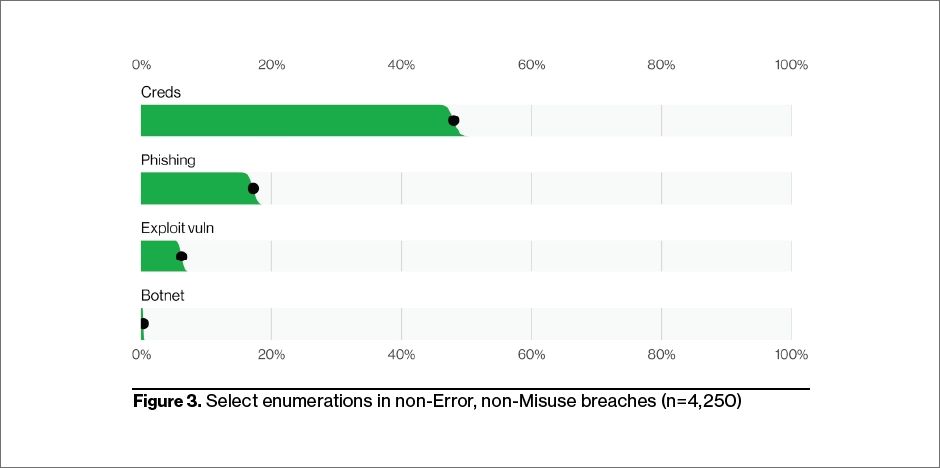
According to the Verizon’s 2022 Data Breach Investigations Report (DBIR), external threat actors were responsible for 90% of the cybersecurity attacks in North America. Across over 4,500 actual incidents, the attacks focused on stealing credentials, phishing into the network, exploiting vulnerabilities and using botnets. No organization is safe without a strategy of protecting from all four threats.
What security is included in SPOT Managed IT Services?
| SPOT Managed IT Services | Included |
|---|---|
| Automated hardware and software inventory lists | |
| Tracking of system documentation, including passwords | |
| Periodic review of active user accounts | |
| Periodic review of network share permissions | |
| Next Generation AntiVirus with additional controls | |
| Online end-user security awareness training | |
| Configure firewalls for perimeter security | |
| Email protection (SPAM filter, encryption) | |
| Monthly patching of Windows updates | |
| Monthly updating of applets, like Acrobat Reader | |
| Review of server backups (central management) | |
| Quarterly device configuration backups | |
| Assigned fractional CIO as Security Officer |
Managed Security Services are needed for some organizations
| SPOT Managed Security Services- Enhanced security | Included | Add-ons |
|---|---|---|
| Additional password protection, using multi-factor authentication | ||
| Additional password protection, identity access management enhancements such as single sign on, password managers | ||
| Additional password protection, analyzing deep web breaches | ||
| Additional data protection, managing BitLocker whole disk encryption | ||
| Additional user training, simulating phishing attacks to test users | ||
| Additional testing, application scan, wireless testing, other | ||
| Additional testing, vulnerability scanning hosts and devices | ||
| Additional testing, external penetration test | ||
| Additional testing, cybersecurity risk assessment | ||
| Additional testing, micro cybersecurity assessment (lite) | ||
| Additional monitoring, per site security log review sensor (SIEM) | ||
| Additional monitoring, cloud monitoring of Office 365 security | ||
| Additional monitoring, 24 x 7 Cyber Security Operations Center |
