iPhone Exploit: Wifi-Takeover Vulnerability Explained
Apple had a security vulnerability – which was patched in May – that could have allowed potential hackers to get complete access to a person’s iPhone — everything from viewing

Apple had a security vulnerability – which was patched in May – that could have allowed potential hackers to get complete access to a person’s iPhone — everything from viewing

Microsoft is urging users to abandon telephone-based multi-factor authentication (MFA) solutions like one-time codes sent via SMS and voice calls and instead replace them with

Here’s a quick-and-easy to consume infographic that illustrates the most common ways patients and medical practitioners access health-related data using technology – and some good
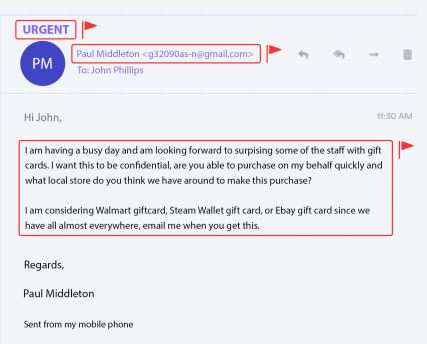
Business Email Compromise Scams are hitting small businesses more than ever. You may have direct experience with this type of cybersecurity attack, but if you’re

Every business goes through their crisis moments. Here’s a summary of 5 suggestions that help managers during our current Covid crisis, looking to leverage the
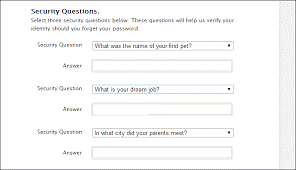
There’s no doubt that our online identities are continuously under attack. The proof is the trillion dollars in profits that cybercriminals will make this year

The awkward toasts. The French press and cocktail shaker close-ups. Even the cats who scamper in from off-screen. If you’re like many people who used

Cybersecurity is More Important than Ever during these extraordinary times. Cbercriminals are exploiting the fears of the Coronavirus pandemic, and have ramped up their cyber

Read article in its entirety here. For the first month of working from home, many employees were in a state of semi-shock; so much energy

Perhaps you’re parents of younger kiddos, or your college kiddos are back in the house again, or you care for extended family members, or you