
Verizon’s 2024 Data Breach Investigations Report was just published. It is one of the most important reports that we receive in the cybersecurity world, because it reports on real-world cybersecurity incidents, which help us understand the most common threat actors, the tactics they utilize, and the targets they choose.
From year to year, we see new and innovative attacks as well as variations on tried-and-true attacks that still remain successful. From the exploitation of well-known and far-reaching zero-day vulnerabilities, such as the one that affected MOVEit, to the much more mundane but still incredibly effective Ransomware and Denial of Service (DoS) attacks, criminals continue to do their utmost to prove the old adage “crime does not pay” wrong.
How Cybercriminals Gain Access
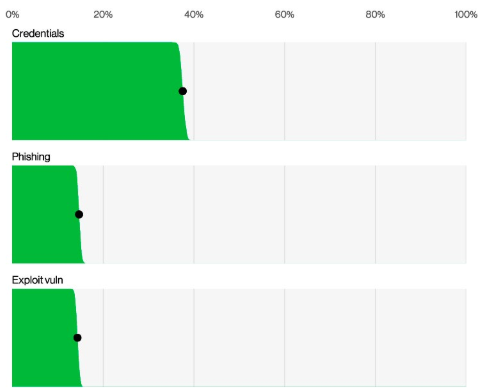
Stolen and compromised credentials as well as phishing emails continue to be major method of gaining access, but exploiting vulnerabilities had a 180% increase from the previous year.
Ransomware & Extortion Trends
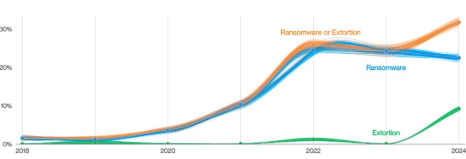
Roughly one-third of all breaches involved Ransomware or some other Extortion technique. Pure Extortion attacks have risen over the past year and are now a component of 9% of all breaches. The shift of traditional ransomware actors toward these newer techniques resulted in a bit of a decline in Ransomware to 23%. However, when combined, given that they share threat actors, they represent a strong growth to 32% of breaches. Ransomware was a top threat across 92% of industries.
Breach Involvement

Breaches involving a human element stayed steady from year to year, and still proves that our people are the biggest cybersecurity threat. 3rd party involvement in breaches increased by 68% from the previous year. And breaches involving errors is probably more prevalent than what we hear about in the press.
Phishing Rates
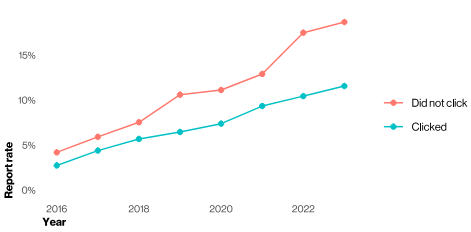
The median time to click on a malicious link after the email is opened is 21 seconds and then only another 28 seconds for the person caught in the phishing scheme to enter their data. This leads to an alarming finding: The median time for users to fall for phishing emails is less than 60 seconds.
Ransomware Impact
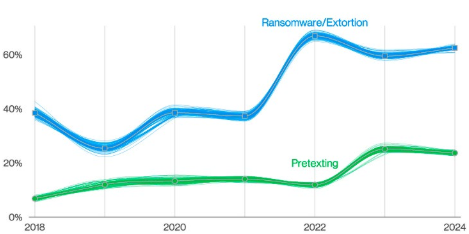
Over the past three years, the combination of Ransomware and other Extortion breaches accounted for almost two-thirds (fluctuating between 59% and 66%) of those attacks. We also found from ransomware negotiation data contributors that the median ratio of initially requested ransom and company revenue is 1.34%, but it fluctuated between 0.13% and 8.30% for 80% of the cases.
Similarly, over the past two years, we have seen incidents involving Pretexting (the majority of which had Business Email Compromise [BEC] as the outcome) accounting for one-fourth (ranging between 24% and 25%) of financially motivated attacks. In both years, the median transaction amount of a BEC was around $50,000.
Lessons Learned
There’s more data in the full report, so please make sure to download it and read it. But here are some key lessons learned for business owners.
- Your people are still the biggest threat. You can make a difference as a business leader by setting the example (follow procedures, take cybersecurity training, provide budget to your IT team for cybersecurity), and by ensuring that all of your people receive regular cybersecurity training, phishing simulations to test their understanding of the training, and Dark Web monitoring and alerting when credentials are compromised on the Dark Web.
- Cybercriminals are getting more aggressive. Cybercriminals are no longer satisfied with encrypting your data and requesting a ransomware. They are now going with multiple extortion to ensure you pay. They will exfiltrate your data and use that data against you – threaten to publish your data, contact your vendors, and clients, and even go so far as to threaten your key employees, all in an effort to make you pay.
- Patching and updating vulnerabilities is more important than ever. There are more Zero Day vulnerabilities being discovered than ever before. It is important to monitor for missing software updates and patch those as soon as possible.
- 24×7 Cybersecurity Monitoring is a requirement in today’s business environment. With the increase in volume and sophistication of cyber attacks, and the resulting increase in cyber risk, utilizing a 24 x 7 Cybersecurity Monitoring service is highly recommended even if not required by your Cyber Insurance or compliance requirements.
Concerned about your cybersecurity risk? Reach out for a complimentary Cybersecurity Discovery Call to learn more about possible solutions.
