
The City of Dallas suffered a major ransomware attack in early May, purportedly responsible by the cybercriminal gang Royal. The impact to the City’s operations has been substantial, with many City services still affected as of this date. 911 dispatchers had to switch to manually documenting received reports rather than submit them via their computer-aided dispatch system. The Dallas Police Department website was offline, along with other systems. The City of Dallas Municipal court remains closed, and some police evidence has not been available for pending trials.
While City officials have said no data was leaked, the cybercriminal gang Royal threatens to release data the group claims to have accessed from the City of Dallas IT systems. The data threatened to be released includes personal information about city employees, information about court cases, medical information, and thousands of government documents.
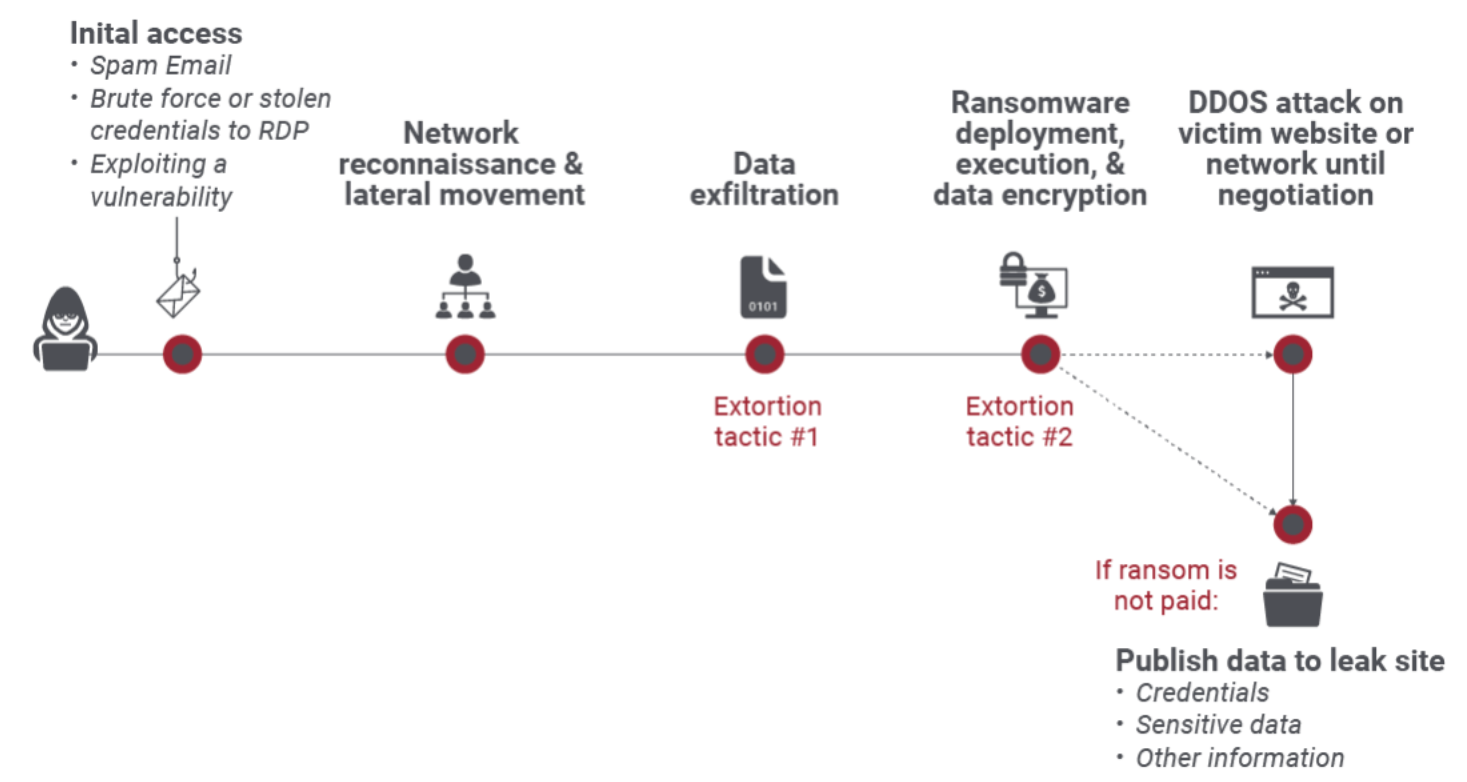
When ransomware attackers encrypt a victim’s data AND threaten to publish stolen data, this is known as Double Extortion Ransomware. This provides the victim with two reasons to pay the ransom.
How You Can Protect Your Organization
Cybercriminals continue to gain access to victim’s networks through:
- Email Phishing Attacks
- Malware
- Vulnerability exploits
- Stolen Credentials posted on the Dark Web
You can reduce the likelihood of a ransomware attack by implementing these cybersecurity measures:
- Conducting an External Penetration Test Regularly – Conducting an external penetration test can help you understand how many ways an attacker could potentially gain access to your network. Reducing the attack surface goes a long way to preventing cyber-attacks.
- Implementing a Comprehensive End User Security Awareness Program – Your people will always be the weakest link when it comes to cybersecurity. Requiring them to complete annual cybersecurity training, giving them timely micro trainings about the latest threats, sending them phishing simulations to find out who needs additional training, and monitoring the Dark Web for possible stolen credentials can make your employees more secure and less likely to fall for a Phishing attack.
- Implementing Multi-Factor Authentication – Let’s face it, most users won’t use unique, random passwords across all of their systems. Implementing Multi-Factor Authentication against not only email but other local and cloud systems and applications can be the single most important cybersecurity protection for your organization.
- Implementing an Effective Patching Strategy – Windows patching is important. So is patching your applications on your network, everything from critical line of business applications to underlying systems software to productivity apps like Acrobat and web browsers. And don’t forget to have a strategy for patching the firmware and software on devices such as servers, firewalls, Wireless Access Points, and other network equipment.
Want to learn more about what your organization can do to improve your cybersecurity posture? Schedule a complimentary Cybersecurity Discovery call with us.
