Contributed by David Johnson
The CIS Critical Security Controls are a recommended set of actions for cyber defense that provide specific and actionable ways to stop today’s most pervasive and dangerous attacks. A principal benefit of the Controls is that they prioritize and focus a smaller number of actions with high pay-off results. They were created by IT security experts who know how attacks work to answer the question, “what do we need to do to stop known attacks.” That group of experts reached consensus and today we have the most current Controls. The Controls take the best-in-class threat data and transform it into actionable guidance to improve security in cyberspace. Too often in cyber security, it seems the “bad guys” are better organized and collaborate more closely than the “good guys.” The Controls provide a means to turn that around.
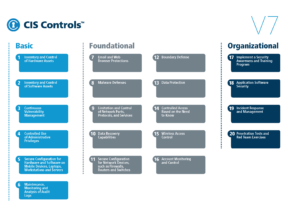
Below are the top 3 ways that Fulcrum Group’s SPOT Monitoring Platform can provide assistance in implementing and supporting the Top 20 CIS Critical Security Controls.
#3 – Inventory and Control of Hardware Assets
Actively manage (inventory, track, and correct) all hardware devices on the network so that only authorized devices are given access, and unauthorized and unmanaged devices are found and prevented from gaining access. SPOT Network Monitoring provides automated hardware asset reporting.
#2 – Inventory and Control of Software Assets
Actively manage (inventory, track, and correct) all software on the network so that only authorized software is installed and can execute, and that unauthorized and unmanaged software is found and prevented from installation or execution. SPOT Network Monitoring provides automated software asset reporting.
#1 – Malware Defenses
Control the installation, spread, and execution of malicious code at multiple points in the enterprise, while optimizing the use of automation to enable rapid updating of defense, data gathering, and corrective action. SPOT Network Monitoring can deploy and report on antivirus software installation, and alert you if computers in your organization are missing antivirus software.
All SPOT Managed IT Services clients automatically receive SPOT Network Monitoring as part of their contract. If you have questions, always feel comfortable giving us a shout.
