See image fullsize.
Cybersecurity is More Important than Ever during these extraordinary times. Cbercriminals are exploiting the fears of the Coronavirus pandemic, and have ramped up their cyber crime activities, especially phishing.
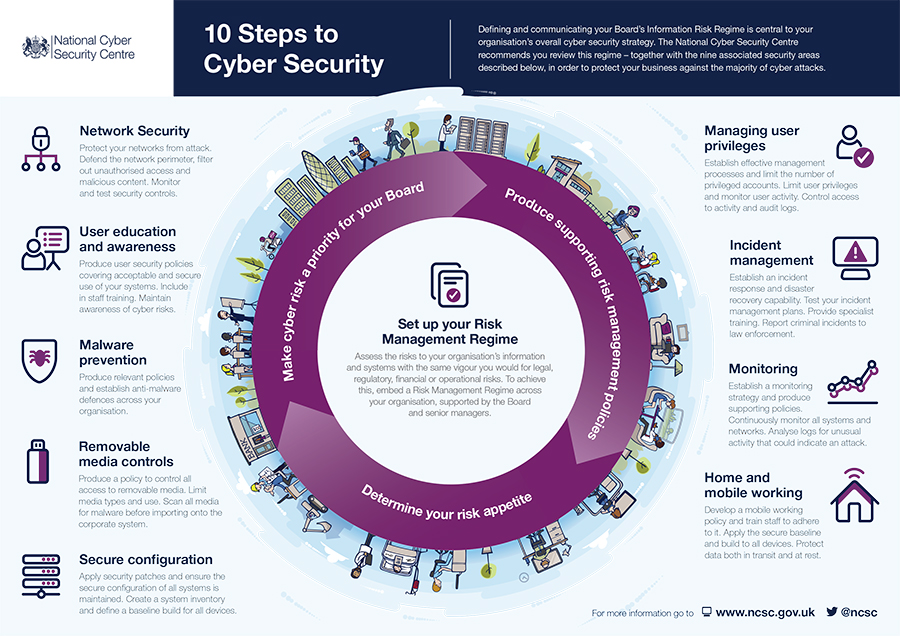
The UK’s National Cyber Security Centre recently released their 10 Steps to Cyber Security. It covers cybersecurity basics and best practices that any size organization can follow. Below are the 10 steps and why they are important.
- Setup Your Risk Management Regime
Make cybersecurity a corporate executive level priority, and regularly assess the risks to your organization and update your risk management policies pertaining to cybersecurity. This will ensure that cybersecurity has a top down approach within your organization. - Network Security
Securing your network perimeter, reducing your attack surface, and monitoring security controls can reduce the ability of cybercriminals to reach your private network. - User Education & Awareness
Your people are typically your weakest link when it comes to cybersecurity. Making sure employees understand your acceptable use policies and providing them with regular cybersecurity training can reduce the number of breaches caused by employees. - Malware Prevention
Centrally managed antivirus combined with additional end point security such as DNS protection paired with managed Windows patching and appropriate workstation permissions can significantly reduce malware infections. - Removable Media Controls
Enforceable policies that restrict access to removable media combined with properly configured antivirus that can scan removable media for malware before copying files to your private network. - Secure Configuration
Not only do Windows devices need to be patched and secure, so do all of your network devices like printers, firewalls, switches, WiFi, network storage. And don’t forget your IoT devices, which continue to be a huge security hole in many private networks. - Managing User Privileges
Regular reviews of user privileges and limiting the number of user accounts with admin or elevated privileges can limit malware/ransomware damage, and also reduce internal data breaches. - Incident Management
The old saying goes, “Everyone has a plan until they are punched in the mouth”.
A cyber attack or breach certainly qualifies as a punch in the mouth. Having a detailed Incident Response Plan ensures that you have a consistent, rational response to an attack or breach. - Monitoring
Without effective cybersecurity monitoring, a cybercriminal could spend days, weeks, or even months in your IT systems without being detected. - Home & Mobile Working
During the coronavirus pandemic, many if not most organizations quickly shifted to remote work scenarios where users are connecting to private corporate networks from personal devices and networks that may or not be secured. Implement an effective policy, require your employees to follow it, and make sure they have refreshed their end user security awareness training.
